Steganography is based on hiding data inside otherwise inconspicuous files, such as hiding text within a text file of an image, hiding information in meta-data, etc.
Tools
There are many tools for steganography.
On this site, I've used openpuff. since it's free and high quality.
It can be used on pretty much any file, but I've only used it for images.
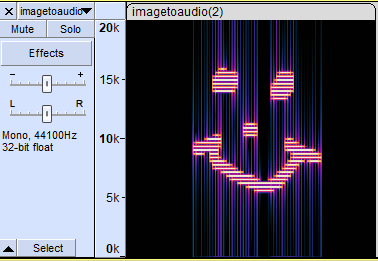
Audio Spectrogram
A spectrogram is a way to view audio that is similar to music notation.
Higher frequencies are shown above lower frequencies, and differences in intensity are shown through colour.
Since with this you have two dimensions to work with (x being time and y being pitch), you can draw images with sound! Use this site. to test it out!
To view these, you can use audio editing programs such as Audacity.
Substitution cyphers are a type of code that substitutes letters (or numbers) of the plaintext (the unencrypted message) with other letters, numbers or symbols. The outcome is known as the cyphertext.
A1Z26 Cypher
This substitution cypher assigns numbers to letters so that:
a is 1,
b is 2,
. . .
z is 26.
Of course, numbers may vary depending on the letters of the alphabet.
Alternatively, the alphabet could start with numbers other than one.
Caesar Cypher
The Caesar Cypher shifts the alphabet a set number of times:
Hadpsoh (“Example” shifted three times)
To solve this, we need to shift all letters forward three times, so that H is E, a is x, and so on.
Now when you have numbers and symbols in your encrypted message, since there usually isn’t really an order to go off of, people typically use ASCII.
According to Santoslove in their Caesar Cypher tutorial:
“[ASCII] is a code that connects each character to a number between 32 and 127. The numbers less than 32 refer to ‘unprintable’ characters, so we will not be using them.”
With this, if we were to encrypt the following sentence by shifting it four spaces back (subtracting four from their number from the ASCII table) we would get:
Hello World! → Dahhk{Sknh`
Vigenère Cypher
It works similarly to the Caesar cypher, but instead of shifting all letters one set amount, they all shift in different increments depending on a given key. For example:
example → wrpqine
key: supercalifragilisticexpialidocious
“s” is the 18th letter of the alphabet (counting from 0), so we shift “e” 18 times: w
“u” is 20th letter of the alphabet (counting from 0), so we shift “x” 20 times: r
“p” … a : p
“e” … m : q
“r” … p : i
“c” … l : n
“a” … e : e
Book Code
The book code is a way to find a specific line and letter of a book, for exampl:
8:20 would be line 8, and 20 characters over.
Moreover, the bible uses a similar way to find passages, for example, Ezikiel 23:20 is the 20th verse of the 23rd chapter of the book of Ezekiel.
This code was used very frequently in the famous Cicada 3310 ARG

